In today’s digital world of 2024, the issue of using VPNs while working remotely has become especially relevant. VPNs are essential for protecting confidential information and maintaining privacy in the virtual setting. VPNs protect remote workers from cyber threats by providing secure access to corporate networks and assets through robust encrypted connections. Considering the growing prevalence of remote work, understanding the need for a VPN while working remotely is absolutely crucial to ensuring that both personal and professional data is protected.
What is a VPN, and Why Do I Need a VPN for Remote Work?
A virtual private network (VPN) is an integral tool, especially during current digital times, offering a secure and private connection between a user’s device and the Internet. By creating an encrypted tunnel, a VPN while working remotely ensures that all online activities, browser data, and personal information remain confidential and inaccessible to third parties. This encryption acts as a security barrier, protecting users from potential cyber threats such as hacking, surveillance, and data theft. VPNs effectively hide a user’s IP address, making it difficult for ISPs, advertisers, and attackers to track or monitor online behavior. VPNs while working remotely also allow users to circumvent location-based restrictions and access content that may be censored in their region, enhancing the freedom and accessibility of the Internet.
In the context of remote work, VPNs play a crucial role in maintaining the privacy and security of cooperative instruments, administration, multiple services, and of course employees who are working outside of the traditional office environment. With the growing popularity of remote work, VPNs provide remote workers with a secure environment to connect to corporate networks and services safely, no matter where they are physically located. This is especially important when accessing confidential company data or communicating with colleagues over public Wi-Fi networks, where the risk of data interception and leakage is increased. In addition, VPNs ensure that remote workers can remain productive and efficient while working remotely by providing seamless access to company resources and programs. VPNs are extremely beneficial for ensuring the privacy, security, and productivity of remote workers in today’s networked digital environment to work remotely using a VPN and work from anywhere with a VPN.
Advantages of Using a VPN for Remote Work
The rise of remote work in recent years has brought to focus the key role of virtual private networks (VPNs), which provide secure connections to company networks and protect against cyber threats.
When working remotely, especially on unsecured or public networks, the risk of unauthorized access to confidential company data increases significantly, creating potential threats to the integrity and confidentiality of the network. Here are the advantages why use a VPN while working remotely at home:
| Access Control | VPNs help businesses manage and control access to corporate networks by allowing fine-tuning permissions for different teams and individuals. By controlling access to corporate resources, a VPN working remotely ensures that only authorized personnel can access sensitive data, increasing network security and integrity. |
| Enhanced Cybersecurity | Using a VPN for secure remote working greatly enhances cybersecurity by encrypting internet connections and converting traffic into unreadable code, which protects online activities from hackers and unauthorized access. The encryption technology used by VPNs ensures that company data and documents remain protected, providing peace of mind for work remotely using a VPN. |
| Secure Remote Access | VPNs create secure tunnels between devices and the company’s network, providing secure communication and access to internal resources, servers, and databases from anywhere in the world. This secure connection ensures that remote employees can conveniently connect to company networks no matter where they are physically located and work remotely using a VPN. |
| Protection While Connected to Public Wi-Fi | Public Wi-Fi networks present major security risks, exposing remote workers to cyberattacks such as malicious twin attacks. VPNs protect data from potential threats on unsecured networks by preventing unauthorized access and data theft, thus ensuring data security and integrity. |
| Avoid Data Throttling | VPNs prevent data throttling by hiding users’ IP addresses, thereby circumventing malicious Internet speed throttling imposed by ISPs. By providing stable Internet speeds, VPNs increase the productivity and efficiency of remote workers, ensuring uninterrupted workflow and communication. |
| Protect Your Data and Identity | VPNs not only protect company data but also protect personal information and identity when working remotely. By encrypting the Internet connection and masking the user’s identity, VPNs prevent data leaks and protect against phishing schemes and identity theft, ensuring online security. |
VPNs offer many benefits for remote workers, from enhanced cybersecurity and secure remote access to protection against data throttling and internet restrictions. As remote work continues to develop, VPNs for remote work play a vital role in ensuring the privacy, security, and productivity of remote workers in developing virtual landscapes.
What is a Site-to-Site VPN?
Site-to-site VPNs are frequently used by companies with multiple offices in different geographic locations that need to access and use the corporate network regularly. A firewall VPN establishes a secure connection between two or more networks, such as a corporate network and a branch office network, enabling uninterrupted communication and resource sharing. In contrast to remote access VPNs, which offer temporary connections for individual users, site-to-site VPNs establish permanent encrypted connections between offices, usually configured as IPsec network connections between network devices. Typically, companies have used site-to-site VPNs to connect the corporate network to remote branch offices, which is especially suitable for scenarios involving in-house data centers, sensitive data, or limited connectivity. However, as organizations increasingly adopt cloud-based applications and mobile workplaces, they are implementing network architectures that bypass the need to route all traffic through a central office. This shift has led to the emergence of Secure Access Service Edge (SASE) solutions that deliver network connectivity and network security services directly through the cloud infrastructure.
SASE offers a variety of security capabilities, including advanced threat prevention, web filtering, and data loss prevention, from a single cloud-based platform. While firewalls are suitable for connecting entire networks or branch offices, remote access to working VPNs allow individual users to securely access corporate networks from remote locations, making them perfect for remote work arrangements from antwhere. Understanding the differences between these types of VPNs is crucial to choosing the right solution for your specific business needs.
The Top Three Most Common VPN Approaches
When using the virtual private network (VPN) landscape, knowing the common approaches is paramount. The three most common working VPN approaches offer a wide range of security, scalability, and operational considerations. Each approach, whether it’s a full tunnel, split tunnel, or cloud proxy, has its unique benefits and limitations that fit different organizational needs. Understanding their strengths will help you determine which one best suits your specific requirements and goals.
Full Tunnel VPN
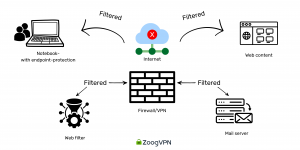
- This method is highly secure but needs more scalability.
- All traffic, including internet-bound traffic, is routed through the corporate network’s security stack.
- Scaling capacity often requires additional hardware, and internet-bound traffic can congest the data center link.
- When using a full tunnel VPN, all network traffic from an endpoint, like a laptop, is directed through a tunnel to a server endpoint within the corporate network. Even internet-bound traffic is routed through the corporate network before accessing the internet, ensuring secure access to corporate resources.
Split-Tunnel VPN
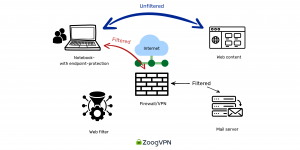
- While more scalable than full tunnel VPN, split-tunnel VPN sacrifices some security.
- Only traffic intended for the corporate data center is routed through the VPN; other internet traffic bypasses the VPN.
- While this approach provides flexibility and scalability, it poses security risks as mobile devices can become potential backdoors into the corporate network.
Cloud Proxy Approach
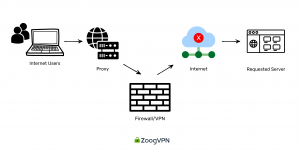
- This method needs both security and scalability.
- Most ports and protocols need to be inspected, leading to subpar security functionality.
- Compliance tools are easily bypassed, and multitenant architectures limit scalability.
- With a cloud proxy VPN, the server is hosted by a cloud provider rather than within the corporate network. This setup either restricts access to cloud-based services or requires exposing on-premises resources to the VPN.
- Employees access corporate resources through an encrypted connection back to the premises, routed through the internet to the cloud provider, before gaining access to resources.
How to ensure your VPN is secure?
VPN tunneling provides secure network access for remote work, but not all solutions provide the same depth of protection. Here are the qualities you should expect from a reliable VPN:
Security: Ensure that your VPN provider prioritizes security by checking the protocol it uses, such as WireGuard, and exploring its attack history. Also, consider factors such as the provider’s location, team size, and experience in the industry. Choosing an open-source VPN service like ZoogVPN adds an extra layer of security with the ability to be publicly verified.
Encryption: Public-key encryption is fundamental to securing communications over VPN tunnels. Evaluate the encryption standards offered by your VPN provider, as strong encryption is vital to protecting data in both transmission and management communications.
Logging Policy: Check the VPN provider’s logging policy to see if they keep any records of your activities. Choose a provider that aligns with your views on data sharing and privacy, ensuring that your sensitive information remains secure and private.
Support: Reliable support is crucial for remote workers relying on VPNs for daily operations. Evaluate the responsiveness of a working VPN provider through social media, review sites, and direct contact to address any technical queries or concerns promptly.
Speed: VPNs cause delays due to traffic routing, but quality providers reduce latency with efficient protocols and sufficient resources. Look for VPN solutions that are optimized for speed to minimize productivity losses caused by network latency.
Simultaneous Connections: For use in an organization, make sure the VPN supports a sufficient number of simultaneous connections for all devices on your network. High-quality VPN solutions offer the flexibility to limit the number of devices, ensuring uninterrupted connectivity for remote teams.
The strength of these attributes often depends on the underlying technology, such as the WireGuard protocol, which is known for its simplicity, security, and performance. Leading VPN services such as ZoogVPN utilize advanced features such as Kill Switch, which prevents data leaks by blocking access to the Internet if the VPN connection is unexpectedly cut off. With ZoogVPN’s commitment to the latest security standards, comprehensive protection is guaranteed. Users can browse the web safely and privately, ensuring that their sensitive information remains protected from cyber threats.
Conclusion
Remote work has become more popular than ever since the pandemic time and the broader shift was done toward employee freedom. However, organizations need to be careful by allowing users to connect directly to internal networks, as it might bring many risks both to individual and company data. To prevent unauthorized access and establish secure connections between devices, it’s essential to set up a home VPN. This allows you to create a private, secure tunnel into your corporate network, ensuring safe remote work from anywhere. Don’t wait—enhance your security and start using a ZoogVPN today!
With so much at stake, you should only use VPNs that have passed an external security review. ZoogVPN is a VPN solution for home, home office, and businesses that works on any device and installs in minutes. Your secure network is created without manual configuration or unstable firewall rules.
Get ZoogVPN to start on your secure remote workspace.